Best SMM Panel for TikTok: Deep Infrastructure Analysis (Protocol 2026)
In the digital marketing landscape, a fundamental misconception persists: users search for the "fastest" or "cheapest" panel, assuming these metrics define efficiency. From an engineering perspective, this is a critical error leading to asset forfeiture.
Summary: The best SMM panel for TikTok is defined by limit control, drip-feed protocols, and behavioral mimicry rather than speed. High-velocity execution triggers algorithmic drops and shadowbans.

Within the TikTok algorithmic ecosystem (Project Texas and global iterations), the concept of "instant execution" is equivalent to the concept of an "attack." The platform's defense mechanisms (Anti-Fraud & Integrity Systems) are calibrated to detect Velocity Spikes, not to evaluate content quality. Consequently, the "best" SMM panel is not a tool for explosive growth, but a sophisticated routing gateway capable of emulating organic behavioral patterns within strict API limits.
Infrastructure Safety Axiom:
"Any activity exceeding the account's natural Trust Score limit and deviating from the normal Time Distribution curve is classified by the neural network as bot traffic, regardless of the signal's actual origin."
This document provides a technical dissection of SMM panel infrastructure exploitation. We replace marketing terminology with engineering definitions to ensure process transparency.
Anatomy of an SMM Panel: Architectural Definition
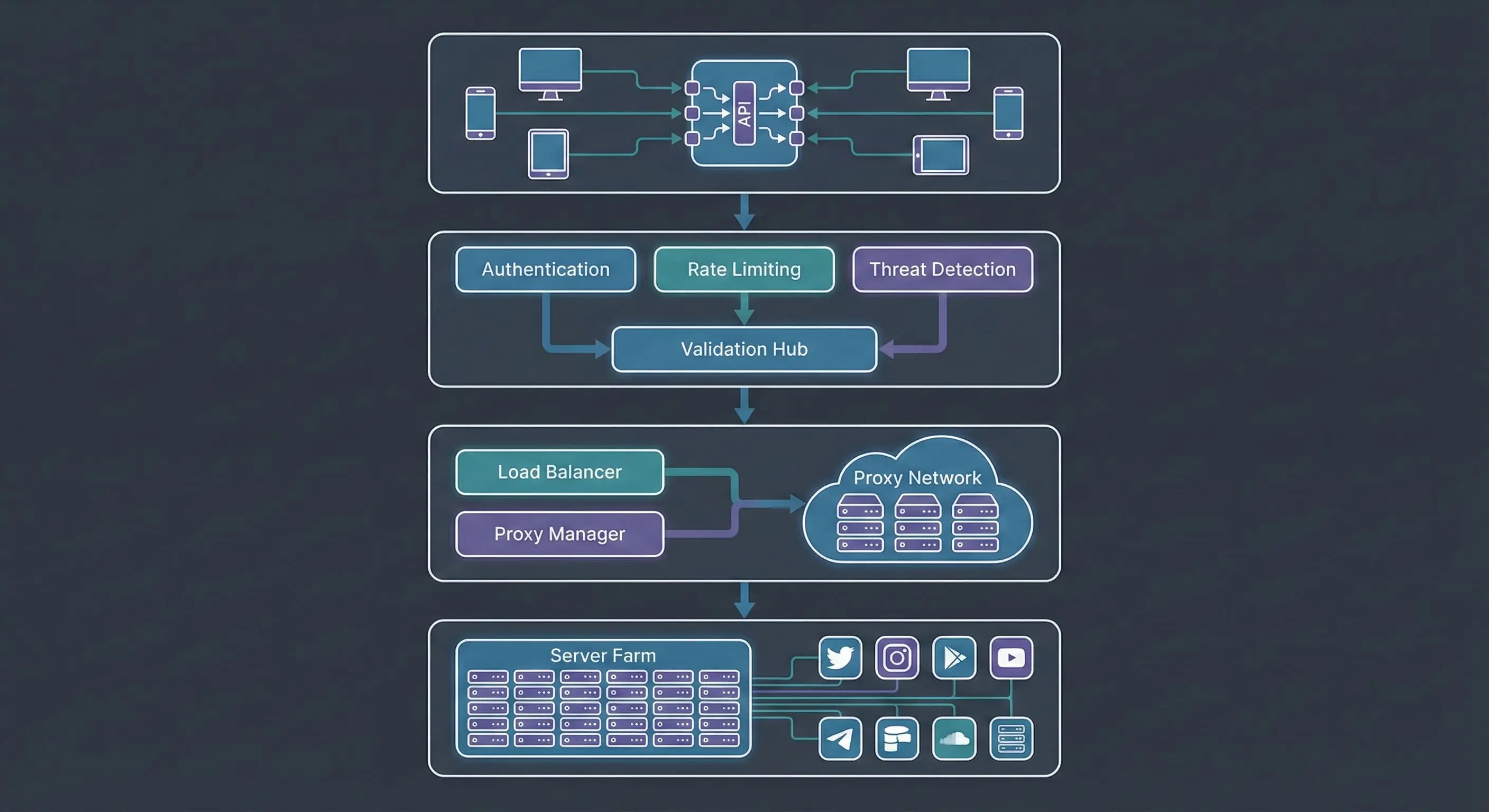
Publicly, services categorized as "SMM Panels" position themselves as service marketplaces. Technically and architecturally, they act as API Aggregators and Request Routing Gateways.
When a user initiates an order, the following chain of events occurs:
- Initialization (Client Layer): You submit a request for 1,000 units (views/likes) via the interface.
- Validation (Validation Layer): The system verifies link availability and current server load.
- Routing (Routing Layer): Your order is transmitted via API to a Direct Provider. The panel you interact with often functions as a Reseller, sub-licensing access to the capacity of wholesale backbone providers.
- Execution (Execution Layer): A server farm or botnet receives the task. Software (bots) begins executing actions utilizing a residential/4G proxy array to mask IP addresses.
Understanding this chain is critical: you are not paying for "popularity," but for machine time and proxy traffic consumption to alter a counter in the TikTok database.
TikTok Defense Mechanics: Velocity-Based Blocking
TikTok employs one of the industry's most advanced Behavioral Biometrics systems. The platform prioritizes the metadata accompanying a signal over the signal itself.
The system analyzes incoming traffic across three primary vectors:
Vector A: Velocity & Acceleration
If an account aged 48 hours receives 5,000 requests per minute, a Rate Limit Abuse trigger is activated. The algorithm deduces: organic traffic cannot scale linearly at such velocity without external referral signals (mentions in high-authority media). Result: Rollback or Shadowban.
Vector B: Session Integrity
High-quality traffic possesses a "digital footprint": cookie history, cache, and a unique Device ID/Fingerprint. Low-cost panels utilize "raw" server-side requests lacking this data. TikTok filters these at the TLS handshake level (TLS Fingerprinting).
Vector C: Retention Rate
A view duration of 0.1 seconds is a definitive "Bot Traffic" signal. The neural network is trained on the premise that a human cannot evaluate content in a split second. If the average watch time of your video drops to zero due to artificial traffic, the video is excluded from the For You Page recommendation engine.
Is SMM Panel Exploitation Safe?
The tool itself is neutral. The danger lies in the exploitation scenario. An SMM panel is safe only when strictly adhering to the "Infrastructure Mimicry" protocol.
Technical Safety Conditions:
- Limit Compliance (Velocity Limits): Do not exceed the permissible action frequency for your account's age.
- Drip-feed Utilization: A technology that fragments a single large Batch into hundreds of micro-transactions spread over time.
- Source Validation: Use mixed traffic where direct hits are diluted with profile visits or search transitions.
Risk Profile:
- High Risk: Deploying 10,000+ views/likes on an empty account within 1 hour. (Shadowban Probability > 90%).
- Medium Risk: Using low-cost "No Refill" services from server-grade IPs. (Drop Probability > 60%).
- Low Risk: Gradual growth (5-10% daily) using Residential Proxies and Drip-feed functionality.
Why Drops Occur and How Data Sanitation Works
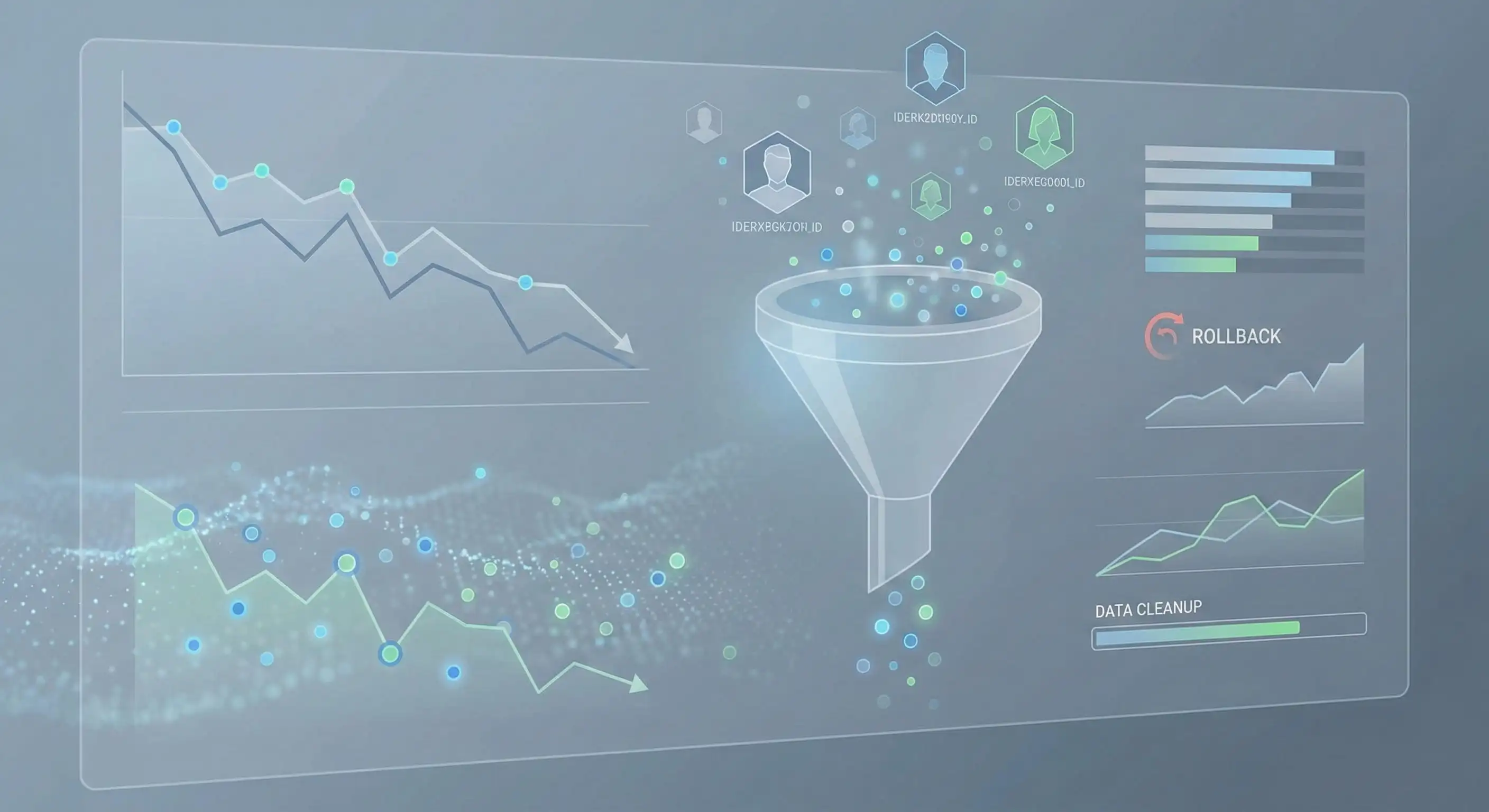
A "Drop" is not a technical failure on the panel side. It is a standard procedure of Data Sanitation performed by TikTok. The platform regularly audits interaction logs.
The Drop Algorithm operates as follows:
- Flagging: The system marks suspicious accounts (bots) exhibiting non-human activity patterns (24/7 liking, zero watch time).
- Cascading Removal: Once a bot account is suspended, all actions performed by it over the last 30-90 days (likes, follows) are automatically nullified.
- Counter Correction: Metrics on your videos are updated to reflect the new reality.
Engineer's Note:
"A 'Refill' guarantee on a panel does not imply immunity to drops. It indicates the provider is willing to absorb the cost of re-sending new requests to compensate for deleted ones. This is an economic safeguard, not a technical one."
Can Panels Be Used Without Bans? (Protection Protocols)
Yes, provided the strategy shifts from "rapid success" to "managed background activity."
Protocol 1: Drip-feed as Standard
Never deploy full volume in a single transaction. If your target is 1,000 likes, configure Drip-feed: 10 runs of 100 likes with a 60-minute interval. This generates a growth curve resembling organic virality.
Protocol 2: Ratio Compliance
The simplest way to trigger a shadowban is to violate conversion mathematics.
Normal Metrics:
- Views / Likes: 10 to 1 (10%).
- Likes / Comments: 100 to 1.
If you have 100 views and 100 likes (100% conversion), the algorithm flags this as an anomaly.
Protocol 3: Diversity Simulation
Do not order likes exclusively. Combine them with Shares and Saves. For the TikTok algorithm, a "Save" is a stronger quality signal than a "Like."
How to Verify an SMM Panel: The "Canary Test" Protocol
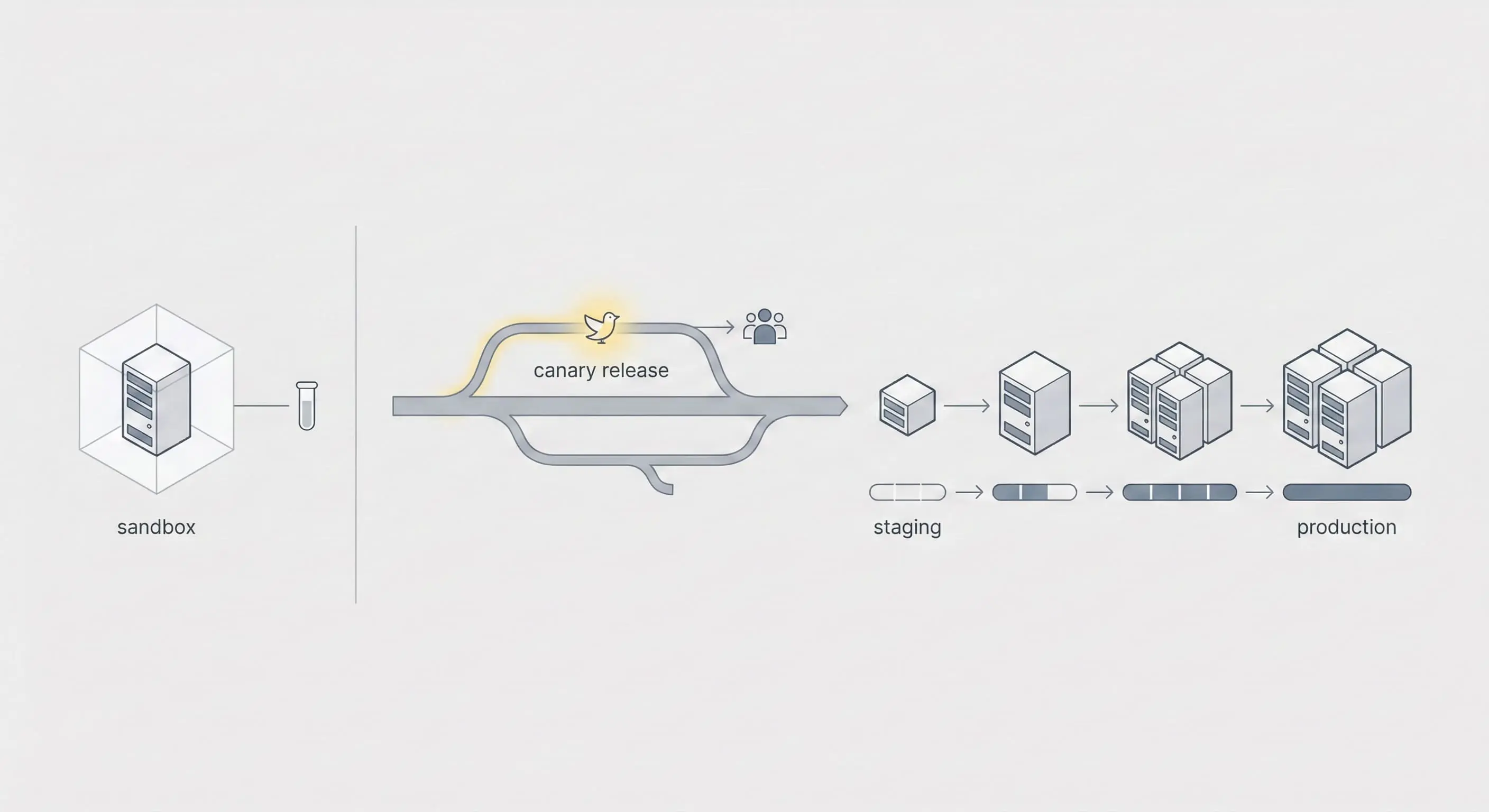
In industrial software development, new code is deployed to 5% of users first (Canary release). In traffic management, you must adopt the same methodology.
Never direct traffic from an unverified provider to a primary asset (Money Site/Account). Use the following testing algorithm:
- Isolation (Sandbox Environment): Create a test account on a separate device or via an anti-detect browser. Upload neutral content.
- Micro-transaction: Order the minimum possible service lot (Server ID). Typically 100-1,000 views.
- Latency Check Phase: Measure Start Time. If the service starts in 48 hours instead of the claimed 1 hour, the provider is overloaded; usage is risky.
- Retention Check Phase: Leave the account for 72 hours. Check analytics. If a drop exceeding 10% occurs, the service is unfit for "white-hat" projects.
- Geo-Data Analysis: Check TikTok analytics. If you ordered US targeting but views originated from Indonesia or Egypt, routing is malfunctioning.
Technical Dictionary and Definitions
- API (Application Programming Interface): A software gateway allowing two applications to exchange data. In the panel context, it is the method of automated order transmission from reseller to executor.
- Drip-feed: A task scheduling mechanism allowing the automated creation of a series of orders with a defined interval.
- Drop Rate: The percentage of interactions removed by the platform after quality verification. "Non-Drop" services are simply those with low detection probability, not "immunity" to removal.
- Shadowban: An account state where content is technically available but artificially excluded from ranking and recommendation mechanisms. Diagnosed by a sudden drop in "For You" reach to zero.
- Server Overload: A state where the request queue exceeds the bot farm's throughput capacity. Results in start delays (Pending status).
Conclusion and Disclaimer
The automation market is an arms race between defense algorithms (TikTok) and circumvention algorithms (Providers). It is a dynamic environment with no constants.
This document describes operational logic and risk mitigation methods. It is not an endorsement of platform rule violations and does not guarantee financial outcomes. Responsibility for software utilization lies with the operator.

